Microsoft Antimalware for Azure Microsoft Docs. The modern threat landscape for cloud environments is extremely dynamic, increasing the pressure on business IT cloud subscribers to maintain effective protection in order to meet compliance and security requirements. Microsoft Antimalware for Azure is free real time protection capability that helps identify and remove viruses, spyware, and other malicious software, with configurable alerts when known malicious or unwanted software attempts to install itself or run on your Azure systems. The solution is built on the same antimalware platform as Microsoft Security Essentials MSE, Microsoft Forefront Endpoint Protection, Microsoft System Center Endpoint Protection, Windows Intune, and Windows Defender for Windows 8. Microsoft Antimalware for Azure is a single agent solution for applications and tenant environments, designed to run in the background without human intervention. You can deploy protection based on the needs of your application workloads, with either basic secure by default or advanced custom configuration, including antimalware monitoring. When you deploy and enable Microsoft Antimalware for Azure for your applications, the following core features are available Real time protection monitors activity in Cloud Services and on Virtual Machines to detect and block malware execution. Scheduled scanning periodically performs targeted scanning to detect malware, including actively running programs. Malware remediation automatically takes action on detected malware, such as deleting or quarantining malicious files and cleaning up malicious registry entries. Microsoft Security Essentials Settings Table' title='Microsoft Security Essentials Settings Table' />Signature updates automatically installs the latest protection signatures virus definitions to ensure protection is up to date on a pre determined frequency. Antimalware Engine updates automatically updates the Microsoft Antimalware engine. Antimalware Platform updates automatically updates the Microsoft Antimalware platform. C370&ssl=1' alt='Microsoft Security Essentials Settings Table' title='Microsoft Security Essentials Settings Table' />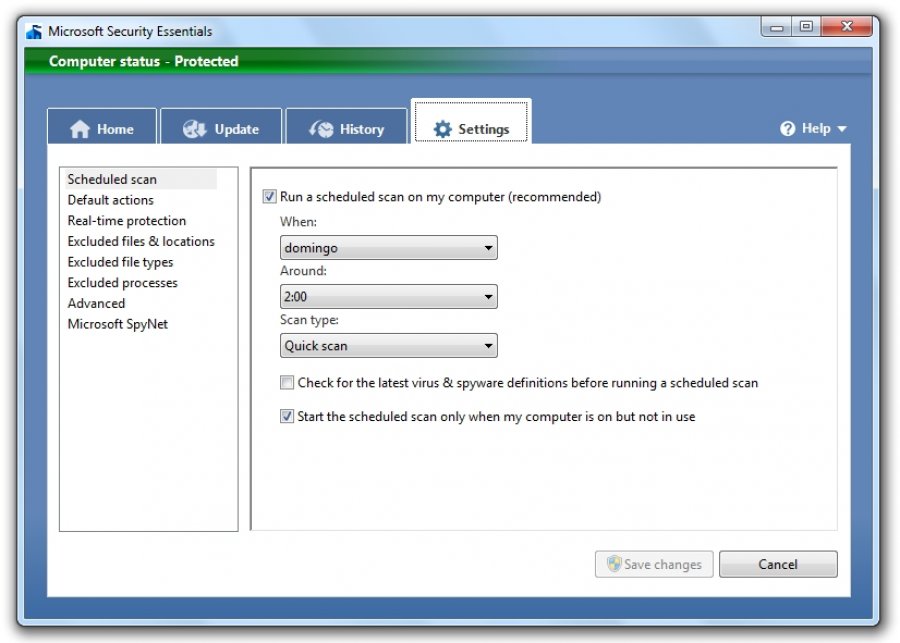 Active protection reports telemetry metadata about detected threats and suspicious resources to Microsoft Azure to ensure rapid response to the evolving threat landscape, as well as enabling real time synchronous signature delivery through the Microsoft Active Protection System MAPS. Samples reporting provides and reports samples to the Microsoft Antimalware service to help refine the service and enable troubleshooting. Exclusions allows application and service administrators to configure certain files, processes, and drives to exclude them from protection and scanning for performance andor other reasons. Antimalware event collection records the antimalware service health, suspicious activities, and remediation actions taken in the operating system event log and collects them into the customers Azure Storage account. Architecture. The Microsoft Antimalware for Azure solution includes the Microsoft Antimalware Client and Service, Antimalware classic deployment model, Antimalware Power. Shell cmdlets and Azure Diagnostics Extension. The Microsoft Antimalware solution is supported on Windows Server 2. R2, Windows Server 2. The privacy dashboard. To use everything on this website, turn on cookies in your browser settings. The TechNet Library contains technical documentation for IT professionals using Microsoft products, tools, and technologies. Windows compares the requested access rights and the information in the threads access token with the information in the file or directory objects security. Learn how Microsoft works to secure your data, protect its privacy, and comply with global standards in Microsoft business cloud services. Windows Server 2. R2 operating system families. It is not supported on the Windows Server 2. Linux. Support for Windows Server 2. Defender has been released, you can read more about this update here. The Microsoft Antimalware Client and Service is installed by default in a disabled state in all supported Azure guest operating system families in the Cloud Services platform. The Microsoft Antimalware Client and Service is not installed by default in the Virtual Machines platform and is available as an optional feature through the Azure portal and Visual Studio Virtual Machine configuration under Security Extensions. Acer Bios Key Windows 10. Microsoft. The fiercely competitive software giant is positioning its wares for cloud computing with software and services. The companys two cash cows operating. At Microsoft our mission and values are to help people and businesses throughout the world realize their full potential. Use these steps to restore your computers security settings to their default configurations. Applies to computers that are running Windows XP and Windows. Manage Security Settings Section. Directly below the Security Essentials section there is a Manage Security Settings Fig. When using Azure App Service, the underlying service that hosts the web app has Microsoft Antimalware enabled on it. This is used to protect Azure App Service infrastructure and does not run on customer content. Microsoft antimalware workflow. The Azure service administrator can enable Antimalware for Azure with a default or custom configuration for your Virtual Machines and Cloud Services using the following options Virtual Machines In the Azure portal, under Security Extensions. Virtual Machines Using the Visual Studio virtual machines configuration in Server Explorer. Virtual Machines and Cloud Services Using the Antimalware classic deployment model. Virtual Machines and Cloud Services Using Antimalware Power. Shell cmdlets. The Azure portal or Power. Shell cmdlets push the Antimalware extension package file to the Azure system at a pre determined fixed location. The Azure Guest Agent or the Fabric Agent launches the Antimalware Extension, applying the Antimalware configuration settings supplied as input. This step enables the Antimalware service with either default or custom configuration settings. If no custom configuration is provided, then the antimalware service is enabled with the default configuration settings. Refer to the Antimalware configuration section in the Microsoft Antimalware for Azure Code Samples for more details. Once running, the Microsoft Antimalware client downloads the latest protection engine and signature definitions from the Internet and loads them on the Azure system. The Microsoft Antimalware service writes service related events to the system OS events log under the Microsoft Antimalware event source. Events include the Antimalware client health state, protection and remediation status, new and old configuration settings, engine updates and signature definitions, and others. You can enable Antimalware monitoring for your Cloud Service or Virtual Machine to have the Antimalware event log events written as they are produced to your Azure storage account. The Antimalware Service uses the Azure Diagnostics extension to collect Antimalware events from the Azure system into tables in the customers Azure Storage account. The deployment workflow including configuration steps and options supported for the above scenarios are documented in Antimalware deployment scenarios section of this document. Note. You can however use PowershellAPIs and Azure Resource Manager templates to deploy Virtual Machine Scale Sets with the Microsoft Anti Malware extension. For installing an extension on an already running Virtual Machine, you can use the sample python script vmssextn. This script gets the existing extension config on the Scale Set and adds an extension to the list of existing extensions on the VM Scale Sets. Default and Custom Antimalware Configuration. The default configuration settings are applied to enable Antimalware for Azure Cloud Services or Virtual Machines when you do not provide custom configuration settings. The default configuration settings have been pre optimized for running in the Azure environment. Optionally, you can customize these default configuration settings as required for your Azure application or service deployment and apply them for other deployment scenarios. The following table summarizes the configuration settings available for the Antimalware service. The default configuration settings are marked under the column labeled Default below. Antimalware Deployment Scenarios. The scenarios to enable and configure antimalware, including monitoring for Azure Cloud Services and Virtual Machines, are discussed in this section. Virtual machines enable and configure antimalware. Deployment using Azure Portal.
Active protection reports telemetry metadata about detected threats and suspicious resources to Microsoft Azure to ensure rapid response to the evolving threat landscape, as well as enabling real time synchronous signature delivery through the Microsoft Active Protection System MAPS. Samples reporting provides and reports samples to the Microsoft Antimalware service to help refine the service and enable troubleshooting. Exclusions allows application and service administrators to configure certain files, processes, and drives to exclude them from protection and scanning for performance andor other reasons. Antimalware event collection records the antimalware service health, suspicious activities, and remediation actions taken in the operating system event log and collects them into the customers Azure Storage account. Architecture. The Microsoft Antimalware for Azure solution includes the Microsoft Antimalware Client and Service, Antimalware classic deployment model, Antimalware Power. Shell cmdlets and Azure Diagnostics Extension. The Microsoft Antimalware solution is supported on Windows Server 2. R2, Windows Server 2. The privacy dashboard. To use everything on this website, turn on cookies in your browser settings. The TechNet Library contains technical documentation for IT professionals using Microsoft products, tools, and technologies. Windows compares the requested access rights and the information in the threads access token with the information in the file or directory objects security. Learn how Microsoft works to secure your data, protect its privacy, and comply with global standards in Microsoft business cloud services. Windows Server 2. R2 operating system families. It is not supported on the Windows Server 2. Linux. Support for Windows Server 2. Defender has been released, you can read more about this update here. The Microsoft Antimalware Client and Service is installed by default in a disabled state in all supported Azure guest operating system families in the Cloud Services platform. The Microsoft Antimalware Client and Service is not installed by default in the Virtual Machines platform and is available as an optional feature through the Azure portal and Visual Studio Virtual Machine configuration under Security Extensions. Acer Bios Key Windows 10. Microsoft. The fiercely competitive software giant is positioning its wares for cloud computing with software and services. The companys two cash cows operating. At Microsoft our mission and values are to help people and businesses throughout the world realize their full potential. Use these steps to restore your computers security settings to their default configurations. Applies to computers that are running Windows XP and Windows. Manage Security Settings Section. Directly below the Security Essentials section there is a Manage Security Settings Fig. When using Azure App Service, the underlying service that hosts the web app has Microsoft Antimalware enabled on it. This is used to protect Azure App Service infrastructure and does not run on customer content. Microsoft antimalware workflow. The Azure service administrator can enable Antimalware for Azure with a default or custom configuration for your Virtual Machines and Cloud Services using the following options Virtual Machines In the Azure portal, under Security Extensions. Virtual Machines Using the Visual Studio virtual machines configuration in Server Explorer. Virtual Machines and Cloud Services Using the Antimalware classic deployment model. Virtual Machines and Cloud Services Using Antimalware Power. Shell cmdlets. The Azure portal or Power. Shell cmdlets push the Antimalware extension package file to the Azure system at a pre determined fixed location. The Azure Guest Agent or the Fabric Agent launches the Antimalware Extension, applying the Antimalware configuration settings supplied as input. This step enables the Antimalware service with either default or custom configuration settings. If no custom configuration is provided, then the antimalware service is enabled with the default configuration settings. Refer to the Antimalware configuration section in the Microsoft Antimalware for Azure Code Samples for more details. Once running, the Microsoft Antimalware client downloads the latest protection engine and signature definitions from the Internet and loads them on the Azure system. The Microsoft Antimalware service writes service related events to the system OS events log under the Microsoft Antimalware event source. Events include the Antimalware client health state, protection and remediation status, new and old configuration settings, engine updates and signature definitions, and others. You can enable Antimalware monitoring for your Cloud Service or Virtual Machine to have the Antimalware event log events written as they are produced to your Azure storage account. The Antimalware Service uses the Azure Diagnostics extension to collect Antimalware events from the Azure system into tables in the customers Azure Storage account. The deployment workflow including configuration steps and options supported for the above scenarios are documented in Antimalware deployment scenarios section of this document. Note. You can however use PowershellAPIs and Azure Resource Manager templates to deploy Virtual Machine Scale Sets with the Microsoft Anti Malware extension. For installing an extension on an already running Virtual Machine, you can use the sample python script vmssextn. This script gets the existing extension config on the Scale Set and adds an extension to the list of existing extensions on the VM Scale Sets. Default and Custom Antimalware Configuration. The default configuration settings are applied to enable Antimalware for Azure Cloud Services or Virtual Machines when you do not provide custom configuration settings. The default configuration settings have been pre optimized for running in the Azure environment. Optionally, you can customize these default configuration settings as required for your Azure application or service deployment and apply them for other deployment scenarios. The following table summarizes the configuration settings available for the Antimalware service. The default configuration settings are marked under the column labeled Default below. Antimalware Deployment Scenarios. The scenarios to enable and configure antimalware, including monitoring for Azure Cloud Services and Virtual Machines, are discussed in this section. Virtual machines enable and configure antimalware. Deployment using Azure Portal.
Blog Posts
- Learner S License Online Mumbai India
- Vlc Media Player 2 0 6 Freeware Game
- Simple Fuel Injector Driver Circuit
- Mio Navigatie Met Gratis Update Tomtom
- Free Wilson Meadows Music Downloads
- Warcraft Orcs Versus Humans Download
- C Programming Software For Windows 7 Home Basic
- Best Software For Axiom 49 Pro
- Waar Kan Ek Gratis Afrikaanse Musiek Aflaai Musiek
- Change Windows Xp Registered Ownership
- Sky Road Game Download For Windows Xp
- Organ Trail Complete Edition I Can T Do It Trophies Unlimited
- Crack For Premiere Pro Cs5 Torrent